On September 17, 2024, approximately 5,000 pagers used by Hezbollah in Lebanon exploded, causing a few dozen deaths and thousands of injuries. Many victims required amputation of fingers. Israeli Prime Minister Netanyahu publically took responsibility for approving this attack on November 11. While many criticized the indiscriminate nature of Israeli tactics (this certainly counts under the FBI's definition of international terrorism), all will agree that this event made the general, tinfoil hat-less public aware of the urgency of securing our supply chains. What happens when instead of a tight American ally blinding and dismembering thousands of members of a labelled international terrorist organization, China or the US inserts a backdoor into every computer in the world?
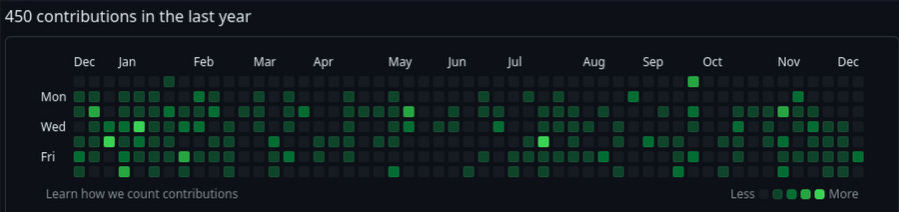
Let's investigate this possibility by looking at the software analogue of supply chain attacks. "Supply chain attacks" in the context of software security refers to a piece of software that is altered by an attacker to contain some sort of vulnerability before it is distributed to a customer. These are infrequently identified, with a few high-profile occurrences in the open-source world. If you're a fan of 90's sci-fi, think of the backdoors put into every important dinosaur-counting, vault-with-stock-certificates-controlling, or humans-as-a-battery-farm-even though-it-makes-more-sense-for-them-to-be-a-server-farm-but-perhaps-that-was-a-dumbed-down-metaphor-because-it-was-1999-and-3-years-before-the-foundation-of-AWS-simulation computers. An attempt at inserting a backdoor into the wildly used xz package was identified in February of this year. A trusted Open Source contributor "Jia Tan" inserted a backdoor into the open source tool used to compress and decompress files that is packaged with most Linux installations. Because it is bundled with default installations of Linux, it's a very juicy target for anyone who possesses the payload to open the backdoor. The backdoor can be activated remotely by interacting with an OpenSSH server. Luckily, this attempt was discovered by an independent party shortly before it was packaged with any major Linux distributions, though some rolling distros were impacted. If the patch slipped through, millions of machines would be backdoored effectively overnight, with the problem of remediation getting more and more difficult the longer the backdoor goes undiscovered. The "Jia Tan" account has been effectively abandoned, with a wayback capture of the github contribution graph from last year looking like this:
As of November 29th looking like this with the red square showing when the malicious commit was made:
Analyses of this backdoor have characterized it as very sophisticated. While most threat intelligence orgs will shy away from publicly calling out suspected state-sponsored attacks without hard proof of attribution, among cybersecurity professionals it is generally accepted that this is not amateur work. It is feasible for well-resourced attackers, like state-sponsored actors, to spend years developing an online persona to cultivate trust with an organization or an open-source project to allow them to slip a backdoor into a widely used package.
The danger of supply chain attacks is their scope. Successfully inserting a backdoor into a package has been shown to be more effective than developing an exploit for an existing package. The SolarWinds attack in 2020 demonstrated this, and we can look to the absolute shitshow that was the Log4Shell event in 2021 to show us how difficult it is to extricate vulnerable software, especially without a working Software Bill of Materials (SBOM). Arctic Wolf (AWOOOOOO!) claimed that the average incident response cost of a Log4Shell incident exceeds $90,000. Hopefully these events catalyzed the industry to utilize SBOMs, but even companies with advanced visibility into their software stack will incur a labor cost in removing a backdoor.
Side Note: I'm digging into some data right now for a separate article title "Corporate Contributors to Open Source" where I analyze Huawei's contributions to the Linux kernel and other software, and their attempts at projecting an outsized impact on the Open Source ecosystem. Watch out for that.
Let's turn our minds to hardware. How would an advanced actor like a state-sponsored Advanced Persistent Threat (APT) execute a similar attack against hardware? To answer that, we need to understand how we make math from sand.
The Semiconductor Supply Chain
Before becoming the brain of the computer you're looking at, the component materials of a chip take a path so complex that its proven impossible to contain the entire supply chain in a single country since at least the 80s. The supply chains involved start on every continent and have massive gathering points in a few geopolitical hotbeds providing single points of failure. The individual chemicals and components that compose a final product will travel between dozens of different countries by land, air, and sea before being assembled into the final product in a Chinese, Indian, Mexican, Indonesian, or Californian assembly facility. Let's go through a quick instruction of the process:
Building Chips Checklist
Building the wafer: Dig up a chunk of 95% Silicon Quartz from North Carolina and refine it to 99.9999% Silicon. Send that silicon to a wafer manufacturing facility in California and melt it to 1700°K. Start spinning it in a centrifuge, and dip a seed crystal a little bit larger than your thumbnail and slowly pull it out to create a cylinder ingot of monocrystalline silicon two meters long and roughly either 200 or 300 millimeters wide. Slice the ingot into discs less than a millimeter thick, polish it to space telescope levels of shine, and ship the wafer to a semiconductor fab in Kaohshiung or Phoenix.
Draw the circuitry: The wafer is coated in a photosensitive layer by a Tokyo Electron coating machine. Place the wafer in a one of the 140-ish Extreme Ultraviolet Lithography machines in the world manufactured by ASML with optics manufactured by Zeiss. Insert a photomask which contains the design of the circuity into the machine. In leading-edge silicon production, that photomask is actually a mirror made of alternating Molybdenum and Silicon layers, with the features drawn with a Tantalum-Nitride absorber layer. An ultraviolet laser is shot at the photomask, and where it's not blocked, the light bounces and reacts with the photoresist on the wafer to allow some of the top layer to become soluble to certain solvents.
Make a die: Etch away the portions of the chip by distributing a "developer" solution in a process called "wet etching" that removes all the portions of the wafer that was hit by the ultraviolet laser. Make the cuts in the wafer more accurate by turning a positively charged halogen gas into plasma and sandblasting the wafer in a "dry etching" machine built by Applied Materials.
Make a semiconductor: Create electron sources and drains around gates by doping the die with Arsenic or Antimony, allowing certain portions of the chip to conduct or resist electricity in different conditions. This creates an arrangement of sources, gates, and drains. Depending on the size of gate, more complex geometries may be necessary as quantum malarkey becomes more important at smaller sizes.
Package and test the die: In a semiconductor packaging facility in Rio de Janeiro, Bangkok, or Ho Chi Minh City, dice the circular wafer into the individual dies. Insert the finished die into a plastic or metal casing that fits the final use case for the device. Connect bonding wires from the die to the inputs of a case. Attach metal interconnects to the casing to allow it to be hooked up to a circuit board. Ship the chip to a testing facility in Kuala Lumpur, where a batch will be tested against a battery of tests to ensure as high test coverage as possible economically. If a batch meets specifications, it will be shipped to an assembly plant in Puducherry or Shenzhen.
Assemble into a final product: The chips combined with dozens of other components like inductors, modems, network cards, printed circuit boards, power supplies, and a housing to create a finished product. The final product will be sent to a retailer in Yancheng, Kuwait, Lagos, Manaus, or Baton Rouge, to be sold to a consumer.
Practically every one of the described processes is a niche occupied by a couple different companies in the ecosystem, with a couple notable monopolies like ASML in the cutting-edge lithography space. The semiconductor supply chain is the most complicated manufacturing-at-scale ecosystem in history, and there exists hundreds of attack vectors that can be used to further the goals of any sufficiently advanced group.
Pounds of ink have been spilled about the threat of physical chip supply chain disruption. Taiwan Semiconductor Manufacturing Company (TSMC) has the majority of its manufacturing capability on Taiwan. If a cross-strait conflict were to go hot between China and Taiwan, then chip supply would certainly be affected. We saw an inkling of this during the Pandemic in 2020 all the way to 2023, where an estimated $500 Billion was lost in the automotive industry due to supply chain disruption in chips.
Overlayed on the physical supply lines that are vulnerable to hot conflict in geopolitically-tense areas, are digital supply lines of information carrying chip designs and order information that coordinate the hundreds of companies in this space to produce the final product. Many companies in the chip ecosystem provides an attack surface to be exploited by advanced attackers to insert their own backdoors into systems.
Generally, the chip industry is bifurcated between designers and fabricators, with a few notable exceptions combining the two halves of the house like Intel. For a graphics card, Nvidia will do the design and work closely with TSMC fabs. As the capital expenditure for building a chip fab has increased, this split of responsibilities has allowed smaller companies to participate in the industry without having to scrounge up the expertise or capital to spin up a fabrication run. These "fabless" firms include Broadcomm, Nvidia, Realtek, Marvell, and hundreds others. These firms maintain relationships with "fabs", businesses and factories that do the dirty work of producing runs of chips.
The two halves of the house in chip fabrication have vastly different attack surfaces. A chip design goes through many stages before it is sent over overseas for fabrication. Chip designers will use more than a dozen Electronic Design Automation (EDA) software applications in their workflow to draft gate layouts, calculate waveforms outputs, simulate logic, and coordinate timing. Any of these software can be exploited to make unseen edits to the chip. Not to mention all these design files are sitting on an FTP server somewhere in the building or on the cloud. A sufficiently advanced attacker would probably have little difficulty infiltrating the network, stealing all the design details for a target chip, developing a trojan in a few weeks, and re-infiltrating the network to implant the trojan in the existing design files before it is shipped to the factor. Chip designers will often download 3rd party intellectual property (3PIP) and open source patterns online without verifying their efficacy, origin, or security. I would posit that there are already undiscovered malicious circuitry in widely-used open source patterns.
On the manufacturing end, an advanced attacker will find a target-rich environment for industrial sabotage. An attacker could swap out a single cell in a photomask, so that only a small percentage of chips on a given wafer are compromised. They could just alter the original plans for the photomask, so all chips include malicious circuitry. A compromised lithography machine could be configured remotely to make a few key copper traces thinner than normal so that wear and tear through electromigration causes a failure after a few months of use.
An attacker could have intelligence that an adversary while run out of a critical component in a SAM system designed in the early 2000's and is willing to buy chips from foreign entities. The adversary could infiltrate the target's supplier, rifle through their emails, and find out when these legacy trailing-edge chips will be rotated in for production at their fab in Taiwan. The attackers could then bring down the factory or individual aging machines that holds up production for 6 months. Towards the end of those 6 months, some of the SAM's would be inoperable, allowing for the attackers to blow up a valuable target like a dockyard, nuclear facility, or cache of specialized hardware that would have been prevented by the presence of functional SAM systems. Or, they could modify the designs of chip so that when sent a specific sequence of bits, it overloads a wire that blows a capacitor, bringing down the system until repairs are complete. This kind of backdoor would be classified as a sequential trojan, where a sequence of events will activate some undocumented behavior. This is opposed to a combinatorial backdoor, which typically will which some portion of the circuitry for uncommon values.
Chips get harder to make requiring more hardware, technology, materials, knowledge, labor, time, and capital. It is already impossible for a single company to know where there chips are coming from, much less the entire DoD, unless the industry adapts to this new threat. Everyone benefits from security, even if it makes the jobs of the most powerful military intelligence agencies on the planet ever so slightly harder. Luckily, private organizations like zeroRISC and Cycuity and non-profits lowRISC and OpenTitan are tackling this issue.
If you would like to learn more about the semiconductor industry, Asianometry on YouTube is your one stop-shop. Humble brag, I first found his videos when he had like 100k views.
Music from this month week
You Really Got Me - The Kinks
INVISIBLE - Duran Duran
Nazi Punks Fuck Off - Dead Kennedys
Barrucada - Heart
Literally all of Joan Jett's discography - Joan Jett & the Blackhearts
Pepas - Farruko
Paper Trail$ -Joey Bada$$
So High - Doja Cat












Bro is spitting, thanks for bringing attention to an issue most people don't talk about! Thanks for shouting out Arctic Wolf too, their Threat Intel/Incident Response unit adds a lot to the cyber world.